The Azure Active Directory user provisioning service integrates with the Workday Human Resources API in order to provision user accounts. Azure AD uses this connection to enable the following user provisioning workflows:
- Provisioning users to Active Directory – Provision selected sets of users from Workday into one or more Active Directory domains.
- Provisioning cloud-only users to Azure Active Directory – In scenarios where on-premises Active Directory is not used, users can be provisioned directly from Workday to Azure Active Directory using the Azure AD user provisioning service.
- Write back email address and username to Workday – The Azure AD user provisioning service can write the email addresses and username from Azure AD back to Workday.
What human resources scenarios does it cover?
The Workday user provisioning workflows supported by the Azure AD user provisioning service enable automation of the following human resources and identity lifecycle management scenarios: Learn more skills from Workday training
- Hiring new employees – When a new employee is added to Workday, a user account is automatically created in Active Directory, Azure Active Directory, and optionally Office 365 and other SaaS applications supported by Azure AD, with write-back of the email address to Workday.
- Employee attribute and profile updates – When an employee record is updated in Workday (such as their name, title, or manager), their user account will be automatically updated in Active Directory, Azure Active Directory, and optionally Office 365 and other SaaS applications supported by Azure AD.
- Employee terminations – When an employee is terminated in Workday, their user account is automatically disabled in Active Directory, Azure Active Directory, and optionally Office 365 and other SaaS applications supported by Azure AD.
- Employee rehires – When an employee is rehired in Workday, their old account can be automatically reactivated or re-provisioned (depending on your preference) to Active Directory, Azure Active Directory, and optionally Office 365 and other SaaS applications supported by Azure AD.
Who is this user provisioning solution best suited for?
This Workday user provisioning solution is ideally suited for:
- Organizations that desire a pre-built, cloud-based solution for Workday user provisioning
- Organizations that require direct user provisioning from Workday to Active Directory, or Azure Active Directory
- Organizations that require users to be provisioned using data obtained from the Workday HCM Training module
- Organizations that require joining, moving, and leaving users to be synced to one or more Active Directory Forests, Domains, and OUs based only on change information detected in the Workday HCM module
- Organizations using Office 365 for email
Solution Architecture
This section describes the end-to-end user provisioning solution architecture for common hybrid environments. There are two related flows:
- Authoritative HR Data Flow – from Workday to on-premises Active Directory: In this flow worker events (such as New Hires, Transfers, Terminations) first occur in the cloud Workday HR tenant and then the event data flows into on-premises Active Directory through Azure AD and the Provisioning Agent. Depending on the event, it may lead to create/update/enable/disable operations in AD.
- Email and Username Writeback Flow – from on-premises Active Directory to Workday: Once the account creation is complete in Active Directory, it is synced with Azure AD through Azure AD Connect and email and username attribute can be written back to Workday.
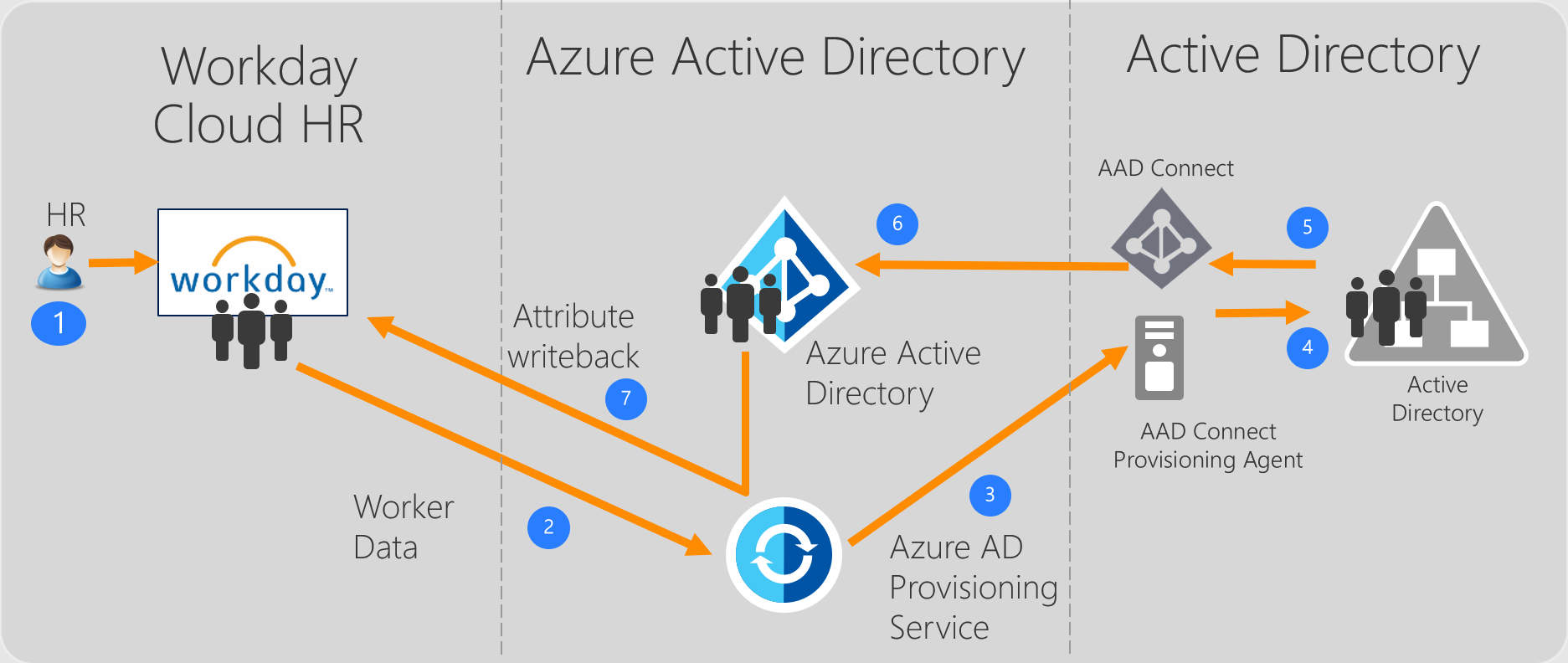
End-to-end user data flow
- The HR team performs worker transactions (Joiners/Movers/Leavers or New Hires/Transfers/Terminations) in Workday HCM
- The Azure AD Provisioning Service runs scheduled synchronizations of identities from Workday HR and identifies changes that need to be processed for sync with on-premises Active Directory.
- The Azure AD Provisioning Service invokes the on-premises Azure AD Connect Provisioning Agent with a request payload containing AD account create/update/enable/disable operations.
- The Azure AD Connect Provisioning Agent uses a service account to add/update AD account data. Get more skills from Workday Integration Training
- The Azure AD Connect / AD Sync engine runs delta sync to pull updates in AD.
- The Active Directory updates are synced with Azure Active Directory.
- If the Workday Writeback connector is configured, it writes back email attribute and username to Workday, based on the matching attribute used.
Planning your deployment
Before beginning your Workday integration, check the prerequisites below and read the following guidance on how to match your current Active Directory architecture and user provisioning requirements with the solution(s) provided by Azure Active Directory. A comprehensive deployment plan with planning worksheets is also available to assist you in collaborating with your Workday integration partner and HR stakeholders.
Prerequisites
The scenario outlined in this tutorial assumes that you already have the following items:
- A valid Azure AD Premium P1 or higher subscription license for every user that will be sourced from Workday and provisioned into either on-premises Active Directory or Azure Active Directory.
- Azure AD global administrator access to configure the provisioning agent
- A Workday implementation tenant for testing and integration purposes
- Administrator permissions in Workday to create a system integration user, and make changes to test employee data for testing purposes
- For user provisioning to Active Directory, a server running Windows Server 2012 or greater with .NET 4.7.1+ runtime is required to host the on-premises provisioning agent
- Azure AD Connect for synchronizing users between Active Directory and Azure AD
Selecting provisioning connector apps to deploy
To facilitate provisioning workflows between Workday and Active Directory, Azure AD provides multiple provisioning connector apps that you can add from the Azure AD app gallery:
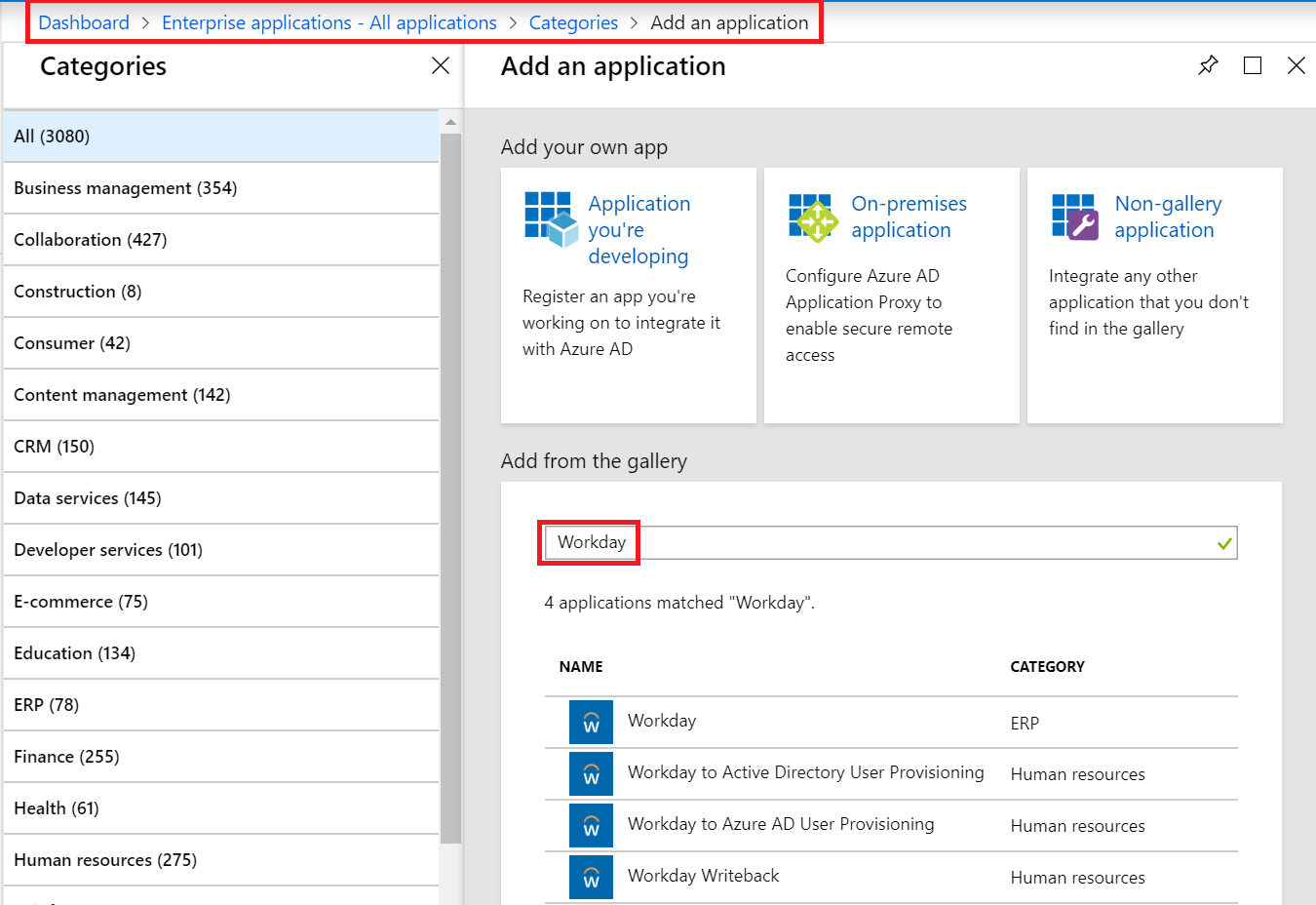
- Workday to Active Directory User Provisioning – This app facilitates user account provisioning from Workday to a single Active Directory domain. If you have multiple domains, you can add one instance of this app from the Azure AD app gallery for each Active Directory domain you need to provision to.
- Workday to Azure AD User Provisioning – While Azure AD Connect is the tool that should be used to synchronize Active Directory users to Azure Active Directory, this app can be used to facilitate provisioning of cloud-only users from Workday to a single Azure Active Directory tenant.
- Workday Writeback – This app facilitates write-back of user’s email addresses from Azure Active Directory to Workday.
Tip
The regular “Workday” app is used for setting up single sign-on between Workday and Azure Active Directory.
Use the decision flow chart below to identify which Workday provisioning apps are relevant to your scenario. 
Use the table of contents to go to the relevant section of this tutorial.
Planning deployment of Azure AD Connect Provisioning Agent
Note
This section is relevant only if you plan to deploy the Workday to Active Directory User Provisioning App. You can skip this if you are deploying the Workday Writeback or Workday to Azure AD User Provisioning App.
The Workday to AD User Provisioning solution requires deploying one or more Provisioning Agents on servers running Windows 2012 R2 or greater with minimum of 4 GB RAM and .NET 4.7.1+ runtime. The following considerations must be taken into account before installing the Provisioning Agent:
- Ensure that the host server running the Provisioning Agent has network access to the target AD domain
- The Provisioning Agent Configuration Wizard registers the agent with your Azure AD tenant and the registration process requires access to *.msappproxy.net over the TLS port 443. Ensure that outbound firewall rules are in place that enable this communication. The agent supports outbound HTTPS proxy configuration.
- The Provisioning Agent uses a service account to communicate with the on-premises AD domain(s). Prior to installation of the agent, it is recommended that you create a service account with domain administrator permissions and a password that does not expire.
- During the Provisioning Agent configuration, you can select domain controllers that should handle provisioning requests. If you have several geographically distributed domain controllers, install the Provisioning Agent in the same site as your preferred domain controller(s) to improve the reliability and performance of the end-to-end solution
- For high availability, you can deploy more than one Provisioning Agent and register it to handle the same set of on-premises AD domains.
Important
In production environments, Microsoft recommends that you have a minimum of 3 Provisioning Agents configured with your Azure AD tenant for high availability.
Integrating with multiple Active Directory domains
Note
This section is relevant only if you plan to deploy the Workday to Active Directory User Provisioning App. You can skip this if you are deploying the Workday Writeback or Workday to Azure AD User Provisioning App.
Depending on your Active Directory topology, you will need to decide the number of User Provisioning Connector Apps and number of Provisioning Agents to configure. Listed below are some of the common deployment patterns that you can refer to as you plan your deployment.
Deployment Scenario #1 : Single Workday Tenant -> Single AD domain
In this scenario, you have one Workday tenant and you would like to provision users to a single target AD domain. Here is the recommended production configuration for this deployment.
To get in-depth knowledge, enroll for a live free demo on Workday Online Training